How to Remove virus "autorun.inf "
I have found this virus very annoying since you cannot open your hard drive or pendrive properly. Most often happen if you want to open any of your hard drive or pendrive you have to open it in explorer by right click the Start menu from then you can go to explorer is it very frustrating unlike what we used to do we just double click any of your media and that’s it. Well before I have search for an answer since I don’t want to format my HDD coz it’s a lot of work to do. I have found some answer in the net that inquire to manually fix the problem, but I have found the easiest way to fix this problem. All you have to do is download this small utility Autorun Eater actually I’m very impress after I download this utility and install my problem solve. I hope in anyway I can contribute this small information and I hope that you will share this small info….. You can find illustration and manual Here
Wednesday, December 31, 2008
How to Remove virus "autorun.inf "
Friday, December 26, 2008
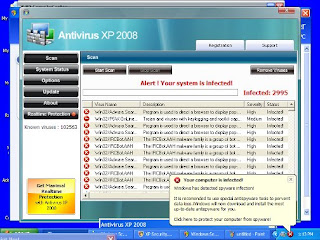
How to remove Spyware ' Anti-Virus XP 2008 '
How to remove Spyware 'Anti-Virus XP 2008
Actually this is not a Anti-Virus. This is just another Spyware that disguise as a virus remover once infected your PC will become slow, pop-up windows keep appearing and it will ask you to register. If not all the annoying thing will happen to your PC. So, I have this small information hoping that it will help you if you encounter this problem.
This is how it looks when you are infected:

Solution :
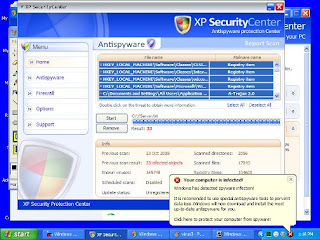
First download the free edition of Malwarebyte’s Anti - Malware don’t worry this is free and I tried and tested this product many times and for sure you don’t want to spend $50 to $80 just to remove this Spyware and yet you don’t want to reformat your pc coz you will loose some important software or data.
This is how it looks when you download the software and install:
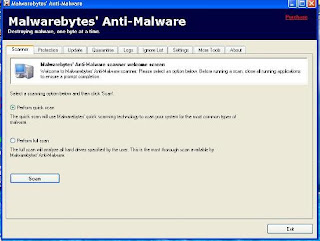
This is how it look when scanning :

Before we scan we need to terminate some files in the taskbar :

Can you see the files that I have circled in red you must terminate or click end process after that then we perform scan
This is how it looks after scanning :

Click remove selected and follow some instruction…. Is that so easy to follow from free utilities but then if like this software you can just click purchase on the upper right corner… that all folks…
Download Your Copy Here
Friday, March 28, 2008
Your Anti Virus
Anti-virus software is used to find, remove or fix files that are infected with computer viruses. Most anti-virus companies release weekly updates of their databases to help keep you safe. Your anti-virus software uses these weekly updates (also known as virus signatures or definitions file) to identify newly discovered viruses.
The most basic anti-virus programs normally have several features to it, the memory resident scan, the system or file scan, and an automated updater. Many more sophisticated programs have many other integration tools that loan in to your instant messengers, your e-mail software and many other programs.
It's very important when you configure your anti-virus software to always make sure you can download new updates every week, if you scan your system for viruses, and your definitions file is out of date it may not even find a problem with your system. Additionally, you should make sure you do in fact scan your system on a regular basis. I personally set my computer to scan around 4 AM so it doesn't bother me.
When you download software, e-mail attachments, or introduce new media (diskettes, cd's, jump drives) in to your system you should scan them before running or viewing them inside another application.
Deciding on which program to use often causes people a lot of head aches. Some anti-virus programs require you to pay each year for a subscription to their virus databases so you can keep your system up to date, others are just expensive out of the box. Additionally, which tends to be the biggest factor in my decision making, is how much resources does the program use.
My favorite anti-virus program for the past couple of years is AVG Anti-Virus, by GriSoft. It's totally free for the personal edition and the updates as well. It has all the major features expected out of an anti-virus suite and is really simple to use and setup.
In the end, it doesn't really matter all that much which program you prefer, but it's very important that you do at least run one!
Wednesday, February 6, 2008
5 Steps to Removing PC Clutter
Its hard enough as it is these days to get organized and then remain that way for weeks and months down the road. We are all very busy people, some of us with 9-5 jobs and one hour commutes, and others of us busy making our lives at home work for us, with children at tow and a variety of chores to do as well as errands to run.
However, no matter how vastly different our lives may be, we all run into the same problems when dealing with organization, and thats: KEEPING organized. need to develop a system that helps your PC remain free of clutter and organized. Granted, this task doesnt come easy at first, but all it takes is a few extra steps each day, done consistently, that will maximize your results in the long run.
So, lets say you have disorganized files all over your hard drive that you have difficulty finding when you need them. Your PC keeps catching viruses out of the blue. You dont know what to do with all your spam mail. You have extra programs and freeware on your PC that you dont know anything about, and even if you did, wouldnt know what to do with them. Here are a few steps to help you get started in the right direction:
1.) Get rid of any unnecessary files or programs that are on your hard drive. This requires a little homework on your part. Youll need to set aside the time to sit down and actually take a look at all of the files on your PC and delete what you dont need. A few things to do periodically for optimal performance is to run a disk cleanup, use your system file checker, and defragment your hard drive.
2.) Organize all of your files and folders. Once youve deleted everything you dont need, take a look at whats left. Is there some way you could organize these in nice categorical folders, so that its easier to retrieve them later on? For example, you could create a few folders underneath your My Documents folder, and give then names such as: My Journal, My TV Shows, My Videos, My Business, My Songs, My JobFind, etc. You could then place all respective files underneath these neatly organized folders. You can also take advantage of many of the folders already supplied to you by Microsoft Windows, such as My Pictures and My Music.
3.) Install adware and spyware programs. I dont think I need to stress how important it is to run antivirus and spyware software. I personally like McAffee because of its wide range of protection services, but Norton AntiVirus works great as well.
4.) Delete unnecessary shareware and freeware files. Its very important to keep your hard drive as clean and organized as possible. Remember that shareware and freeware can potentially be harmful to your computer (viruses!), depending upon which source you received your shareware from.
5.) Delete unnecessary emails and take control of spam. By now, you know to have antivirus software installed on your PC. Thats a must, and will protect you if you should happen to open emails that have viruses attached to them. Before you open any of your emails, check to be sure you know the sender, and that there are no .zip or .exe attachments. Be very careful about opening files with attachments, especially from senders you dont know.
Hope many of these tips will you help you move toward the right direction in de-cluttering your PC, now and for good.
Demetria Zinga is the founder and owner of http://www.faith-media.com, a technology and consulting firm which specializes in web design and hosting, graphics and print designs, internet marketing, and e-training. She is also the founder of http://www.christianladies.net, an interactive ezine, blog, and podcast for Christian women.
Dirty Little Computer Viruses and How To Protect Yourself
Whether you have learned your lesson from a past experience with a nasty computer virus or have been pressing your luck by surfing the web and downloading various files or opening those email messages sent to you by people you dont know without any real understanding of just how vulnerable you really are each time you log onto your computer you now have the opportunity to discover what steps you can take to avoid such an annoying and many times destructive infestation.
Listed below are some of the guidelines you can follow in order to keep those nasty viruses from making a mess out of your computer and your life.
Purchase and install a well respected antivirus software program and be sure to set it up so that it automatically runs when the computer starts up each time.
Make sure to keep your antivirus software up to date by either using the automatic update feature that many come with or make it a habit to manually check at least once or twice a week for updates on your own.
Set your antivirus program to scan for potential viruses each time you open a word-processing document like the ones that get sent through email. Viruses found in word-processing documents are called Macro Viruses.
When purchasing software make sure to only buy from vendors that are well known and from ones you trust.
Resist swapping data with the use of floppy disks or other mobile storage devices between various computers. If exchanging programs between computers is unavoidable just make sure to scan the storage device(s) for viruses before transferring data from one computer to the next.
If using floppy disks to transfer data make sure to format them before using them for the first time.
Never use pirated software. This is both illegal and a very good way to invite an unwanted computer virus.
When downloading software from the internet do so as little as possible. There are many neat programs available on the internet, but unfortunately there are many viruses that go along with them also.
If you must download programs from the internet ALWAYS scan them for viruses BEFORE opening them up to install on your computer.
Probably the most important and neglected method of disaster recovery are periodic backups of all important files found on your computer. Should a virus happen to get through your lines of defense you may need to replace the virus corrupted files with fresh ones that have been kept for such an occasion.
Finally, it is not guaranteed that if you follow the above steps that you will not be the victim of a computer virus, but you can sure bet that if followed you will greatly reduce the chance of being an unsuspecting recipient of such an unwanted program.
Dan Preston is the webmaster of a site called InfoHeaven Digital Books and The Online Book Store where you can find useful and Fr'ee information along with many how-to digital books that cover a large variety of interesting topics. http://infoheaven-digital-books.com and http://online-book-store.net.
How To Take Care Of Your Laptop Computer
As the proud owner of a laptop computer, you'll want to keep your machine in the best possible condition.
Aside from cleaning your screen and dusting the keyboard, however, you'll need to take a few extra steps to maintain your laptop's health:
-- Play it cool
A laptop computer generates a lot of heat, especially when running the latest high-powered software. Too much heat and you risk damaging the internal circuitry.
Always try to keep your laptop in a well-ventilated, cool environment. And ensure you don't block the fan grills on the sides, back, or bottom of the machine at any time.
-- Handle the screen carefully
Avoid touching or playing with your LCD screen.
Yes, it might be fun to watch the waves generated by your finger against the screen, but LCD displays are fragile devices that must be cared for.
Take care when cleaning the screen too, and use only approved cleaning materials.
You won't want to pay the money for screen repairs or, even worse - a new machine entirely.
-- Don't drop it
Whatever you do, don't drop your laptop computer! Keep it safe inside of a carrying case when moving around or traveling.
Don't leave it on the edge of a table or on an unstable support of some kind. One ill fated drop to the floor could spell death for your mobile office.
Try to make sure the rubber feet underneath are in good condition and are still attached. This will prevent the device from sliding around accidentally.
-- Be careful with those drinks...
If you need to have a drink while working or playing, be careful not to spill it.
Your laptop computer could suffer the consequences from just a few drops of liquid poured in the right places.
While you probably do eat and drink around it regardless, you will want to occasionally wipe down the edges, the keyboard, the touchpad, and maybe even wipe down the screen to keep any dirt from accumulating.
-- Just say no to viruses
Security wise, make sure you obtain an anti-virus program.
Secondly, keep it updated!
Buying an anti-virus one month and not updating it for the next six really negates it purpose. Your laptop computer could be exposed to hundreds and thousands of new viruses every month if you don't update your virus definitions.
Most anti-virus programs have automatic update methods, eliminating the need for you to have to remember to do it manually.
-- Avoid Popups
Pop-ups are particularly annoying on a laptop computer. Trying to close a bunch of windows without a regular mouse can be a nuisance.
You'll want a pop-up blocker, such as the Google Toolbar (located at http://tools.google.com), to prevent these pop- up ads.
Many intrusive forms of advertising, and even some viruses, can install software on your machine by using various forms of pop-ups. It's best to get yourself a blocker and avoid the situation entirely.
-- Use a firewall
Always utilize a firewall on your Internet or network- enabled laptop computer. Even if you use Windows XP's built- in firewall (or purchase one from such companies as Norton), your security will greatly benefit from it.
Blocking out all the unnecessary ports and closing all the loopholes will prevent a hacker or virus from freely entering your hard drive.
So there you go. Combine all of the above tactics and help your laptop enjoy a happier and healthier lifestyle!
Free Ways to Tackle Threats to Your Computer
Protect Your PC
Having problems with your pc? Do your kids, family or friends fill it with all the stuff they find on the internet?
Your computer, just like your car, needs to be serviced regularly to keep it running efficiently. You wouldn't fill your car up with petrol from an old rusty can with a layer of dirty water on the bottom, so you shouldn't allow your pc to be treated that way either.
Any pc connected to the internet is a target for viruses, spyware, adware and trojan horses.
You need to protect and clean your pc of these nasties which slow down your costly computer. We will show you how to do at little or no cost in this free report.
Before we start here is our disclaimer:- we take no responsibility for any harm YOU may do to your computer with this information. Use it at your own risk and be sure you are confident of what you are doing before you start. It's a good idea to make a restore point before installing/uninstalling or changing anything (see below for details)
Firstly Viruses, these are the most newsworthy of the baddies, and because of this most people have heard of them. They are the pc version of the Flu, or in a worse case scenario, Sars, and can kill your computer. There are new viruses released almost daily, and you need to keep up to date with Antivirus software to stop them. Fortunately there is a free program which can help you protect your pc. This is called AVG and is available at http://www.grisoft.com just follow links through the site to AVG Free Edition. Register your email address, download and install it to your pc.
The program is pretty straightforward to use but make sure you keep it updated at least weekly by double clicking the AVG icon (four coloured square) in the taskbar and then clicking on update in the window, tick internet as the source and you are good to go. It will automatically update and restart the main Antivirus program. Remember prevention is better than cure though and don't open attachments in emails or even sent to you over instant messengers unless you are sure of the person sending them, even then if you have AVG installed right click the file and use the scan with AVG menu item to double check.
Trojan Horses come next on our hitlist, mostly these are small programs which record either keystrokes or other information and try to send it back to someone to steal your details. But they can be used to take over your pc completely or partially to use your resources to send spam emails, or launch attacks on other computers on the internet, often for denail of service (DOS) attacks. Most Trojan Horses are removed by the AVG antivirus software, or if not it will alert you to its presence, and you can google http://www.google.com to find how to remove it.
A good prevention measure to stop Trojans accessing the net to send their payload is to use a software firewall, again there is at least one free program you can download, called zonealarm. It will ask you wether to allow programs to access the internet or not, meaning if you get something you know you didn't install accessing the net you can tell zonealarm not to allow it. To download zonealarm, go to http://www.zonelabs.com and follow links to the download section, and then to zonealarm (they are not so prominent as the ones for the Pro version which you pay for). It is a good idea to run a firewall to stop attacks coming in from outside as well your details going out. Windows XP with Service Pack 2 installed has a built in firewall, but zonealarm is much more configurable and does a better job overall.
Spyware and Adware can also be responsible for a lot of pc problems. These are often programs piggybacked onto a free download offered to help you with some other task like form filling on websites (Gator is a well known example but they are open about it). Spyware is used by less scrupulous companies and individuals to report back your surfing habits so they can send ads you're more likely to respond to. These slow down your surfing and also run in the background using your pc's power to do their dirty work. Sometimes the information sent back is even more sinister than just your browsing habits, so beware of software you download and check first. Adware is very similar although is usually contained in tracking cookies (small text files downloaded by your browser containing information to track you through a website).
Often these 2 terms are used interchangably. Another nasty which falls in with these is Scumware, which is a term used to describe software which hijacks another program (usually your browser or modem dialler) and displays only content which it's maker wants you to see and often prevents you seeing anything else. The diallers reset your modems settings to dial another (usually very expensive) number rather than your ISP's one. Thankfully some thoughtful individuals have kindly donated their time to give us free programs which will release you from the grip of these fiendish programmers.
Download firstly Adaware from http://www.lavasoft.de and install and run that (if it finds nothing on your pc I would be extremely surprised) secondly download Spybot Search and Destroy from http://www.safer-networking.org/en/download/index.html and install and run that too, it will pop up a dialog to say it has found adaware also on your machine, but it doesn't really mind so close it and continue. As with virus software you should use these and update them both regularly, as you can be sure the people on the darkside of the internet are updating their stuff to keep you hooked into it. Both programs have a button for downloading and installing updates automatically so there is no excuse not to do it before every scan, which we would recommend doing at least monthly and more frequently if possible.
So now you are protected from viruses, trojan horses, and other pc illnesses so that's it right?
Not quite, I have to say one of the most important things on your pc is your personal data, you can re-install Windows, Office and all the other programs on your computer from the cd's, but your prized pictures, your kids half written essay for that all important exam or your wifes recipes handed down from generation to generation carefully typed out and saved can't be. Back it up. NOW. Onto cd's if you have a cd writer or if not get one installed or use floppy discs. But for the sake of your sanity BACK IT UP.
And finally some tips to keep your pc running at its optimum.
Before making any changes to your pc or programs, it's a good idea to make a restore point by going to Start, then accessories on the start menu, then clicking System tools and finally the system restore icon. Follow the prompts and create a restore point to return to if it all goes wrong. Sometimes a slow pc is just the result of too many programs running, close down those you're not using, obvious but often overlooked. If you're anything like most pc users you have a bundle of programs start when your computer does, and sitting in the task tray at the right of the start menu. You can close these down manually but if you don't use them at all then why not remove them?
If you may want them but not everytime you start up you can go to start, then click RUN and in the text box type msconfig without the quotes. Don't worry now this looks daunting but all you need to do is click the tab at the right marked Startup and there is a list of all those programs which run as soon windows starts, now apply a little caution and lookup (http://www.google.com again comes to your aid) any you don't recognise. Now those you're sure you don't need running at startup untick the box.
Next time you start windows will put up a box to tell you you've disabled some things, as long as your pc works ok now, tick the box to not show it again. If you took of something you need or want back run msconfig again, and retick the box in the startup tab again, next time you restart it will return. My last tip is to run defrag monthly, go to start, accessories, system tools and run defrag, this can often speed up a slowing pc as it makes all the files on your hard drive quicker to access.
Douglas Titchmarsh runs several websites, and blogs including http://www.cashinonline.info
Home Business PC Security for Dummies
The Internet is a powerful tool for home-based businesses. If used effectively, it can be your best friend; but if you dont secure your computer, it can be your worst enemy. Im sure youve had your fill of warnings about the latest killer computer virus. So Im not going to harp on about the latest threat, or the potential for damage. What I WILL do is provide some protection tips and links for the layperson.
And now for the obligatory disclaimer: Im no tech-head Im an advertising copywriter and website copywriter. So this article is certainly not definitive or exhaustive. Its simply an overview of some useful and easy to use solutions which should meet most of your requirements. I have no affiliation with the vendors or their distributors, and would encourage people to shop around before buying.)
When you run a home-based business with one or two computers the main things you need to protect against are malicious hackers, worms, viruses, hijackers, trojans, spyware, and adware. For most people, the following tools are all you need.
Firewall e.g. Outpost Firewall Pro
Basically, a firewall stops unwanted stuff getting in. Agnitum Outpost Firewall Pro is powerful and easy to use. You can get it from http://www.agnitum.com/products/outpost/ for USD$39.95. It claims to provide the following protection.
- Detects and blocks all intrusions by hackers
- Blocks data theft attempts
- Operates your computer into stealth mode, making it invisible to intruders
- Analyzes your inbox and Quarantines Internet worms and viruses
- Monitors network activity of your PC
- Protects your children from illegal, inappropriate web sites
- Provides full access to a thorough history of your connections
- Prevents data leak from your PC
- Averts invasions of your privacy through the Internet
- Conceals your surfing habits when browsing the Web
As a general note, your firewall will be the hardest security software to use because it'll ask you a lot of questions, such as:
- Such and such program is trying to connect with such and such server on the internet.
- Such and such server is trying to connect to your computer (these are the ones you have to be very careful of, as they may be people trying to hack your computer).
- A particular application has changed in some way. Do you want to make changed components shared with all other applications which interact with it?
- A program is attempting to change a registry value. Is that ok?
You'll also get a lot of these sorts of questions when you first install the firewall. Once you've set up a few rules, they'll go away because the rules will handle most things.
You can also set the firewall to block active content (javascript, activex, etc.) on websites you visit and emails you receive. If you normally visit only trusted websites and you don't get much spam, you don't really need this feature. But if anyone is visiting dubious sites, or if you get a lot of spam, or you're just very careful, it's a useful feature. TIP: If you do a lot of web surfing, configure Outpost so that whenever you visit a new site, it asks you if you want to allow or block active content (select Options | Plug-Ins Setup, then click Settings, then choose the Exclusions tab and check the box at the bottom of the screen Add Web sites to the exclusions list on the first visit).
Virus Protection e.g. BitDefender 8 (Standard)
Basically, virus protection identifies and quarantines known viruses on your computer. You can get BitDefender 8 (Standard) at http://www.bitdefender.com/bd/site/products.php?p_id=2# for USD$44.95. It claims to provide the following protection.
- Scans and disinfect infected files on access, minimizing data loss
- Allows you to recover infected documents
- Filters against viruses that spread via instant messaging and file sharing software
- Monitors your file system, registry and Internet activity
- Blocks infected e-mail messages
TIP: Set your virus protection up to do a full system scan every night. (If you choose BitDefender, do this by clicking Antivirus from the left of the main window, then clicking on the Scheduler tab.)
Various Free Utilities
Basically, the following tools grab the things the virus and firewall software miss.
- Adaware http://www.download.com/3120-20_4-0.html?qt=adaware&tg=dl-2001. Scans your PC for known data-mining, advertising, and tracking components and cleans your system, so you have more privacy while you surf the Web.
- Spybot - http://www.download.com/3120-20_4-0.html?qt=spybot&tg=dl-20. Searches your hard disk and registry for threats to your security and privacy.
- Spyware Blaster - http://www.download.com/3120-20_4-0.html?qt=spyware+blaster&tg=dl-20. Prevents spyware from being installed on your computer.
- CCleaner - http://www.download.com/3120-20_4-0.html?qt=ccleaner&tg=dl-20. Cleans up junk and temporary files and invalid registry entries and gives you a lot of extra space on your hard drive.
TIP: Update and run each of these utilities at least once a week. Youll be surprised what youll net especially if you havent purchased a full firewall system and anti-virus system.
Conclusion
In my humble opinion, its well worth your while to invest in a firewall application and an anti-virus application. There are a few freeware programs out there that claim to do the same job, but in my experience, they dont quite measure up. And when it comes down to it, theyre so inexpensive especially in comparison to the cost of downtime and/or computer repairs!
Outpost and BitDefender offer online purchases, and send you a license key in an email, which you then use to download the product. You can pay a little extra for them to send you a CD.
The applications listed above certainly arent the only ones available. Im not even claiming theyre the best. But when used together diligently, you should find you have a lot less trouble with your computer, youll have the peace-of-mind of enhanced privacy, and youll minimize the risk of lost income due to downtime.
Good luck!
* Glenn Murray is an SEO copywriter and advertising copywriter, and heads copywriting studio Divine Write. He can be contacted on Sydney +612 4334 6222 or at glenn@divinewrite.com. Visit http://www.divinewrite.com for further details, more FREE articles, or to download his FREE SEO e-book.
You Can Prevent Computer Slowdowns & Issues
Most people understand preventive maintenance like changing the oil in your car will help your car run better and last longer. The same principle holds true for your PC. Based on the computer repair services we do on computers in Cincinnati, we believe 80% of computer slowdowns and problems can be prevented!
The purpose of this article is to help you understand how you can prevent computer slowdowns and other issues.
The top 10 ways you can prevent computer slowdown are
1. Ensure antivirus software is installed, automatically checking for updates, and automatically scanning all incoming files. If there is a virus associated with a new file it will automatically be repaired or quarantined. New viruses come out daily. Because of this, the anti-virus software needs to be configured to automatically updates its self. McAfee and Nortons are the most popular anti-virus software and what we recommend.
2. Run antispyware/antiadware software. Spyware and adware are hands down the most common cause of PC slowdowns. This software is critical if you are surfing the Internet. Spybot Search & Destroy or Ad-aware are the two most common free anti-spyware/adware packages. We recommend a more proactive packages like Spy Sweeper which proactively scans your system and cost less than $30. A combination of Spy Sweeper and Ad-aware provides very good coverage today.
3. Install a hardware firewall to keep hackers out. Hackers have automated tools that are looking for any PC connected to the Internet without a firewall. To give you an idea, at the time of this writing, my home PC was scanned 158 times in the last 24 hours. This means it was scanned an average of every 9 minutes. If youre connected to the Internet but dont have a firewall, hackers (criminals) will be in your PC. Beyond stealing your information they can install programs that can damage or slow your PC down. A hardware firewall to protect all the PCs on the local area network provides the best protection. Recommended hardware firewalls are Linksys, Netgear, and D-link. Hardware firewalls are easier to set up and maintain than software firewalls.
Software firewalls work but we dont recommend them because they are complicated to maintain and often cause other confusion and issues.
4. Microsoft Windows is constantly releasing updates for their operating system. Most of these updates are repairing security holes in their software. You want to configure your machine to automatically check for and download critical updates as they become available.
5. Delete your Internet temp files monthly. This will keep your system cleaner and allow it to run faster.
6. Defrag your hard drive quarterly. This is not the issue it was but there are still benefits to defraging your hard drive on a regular basis.
7. Read the terms and conditions before signing up for or downloading anything for free on the Internet. Free downloads like Kazaa (music), games, toolbars, and coupons often come with adware or spyware. The terms and conditions of downloads explain adware will be installed on the persons machine in exchange for the free software, music, pizza or whatever. Of course, few people read these terms and conditions.
8. Dont open e-mails from strangers. Dont open attachments from people you know if your not expecting it. Call the person and ensure they sent it. If they did not, dont open it. E-mail from strangers and unexpected attachments may contain adware or spyware waiting to install on your computer. It probably wont install if you dont open the e-mail or attachment. (Note: If youre using e-mail software with a mail Preview Pane like Microsoft Outlook, previewing the mail is the same as opening it. You should turn this feature off. Unselect Preview Pane under the View drop down list in Outlook.)
9. Use the Firefox web browser from www.mozilla.org. It is more secure and less vulnerable to popup ads, viruses, computer slowdowns, etc. It also has some additional tab and other options not available with other browsers.
10. Weve talked about preventive maintenance but issues still happen. Hard drives fail. Computers are stolen, etc. Because of these risk, its important to backup your data on a regular basis. The best backups are stored off site. This can be done with an Internet service or store the data to a CD and take it to another location on a regular basis.
In summary, we guarantee regular preventive maintenance will keep your computer running better. We suggest doing these things yourself or schedule a computer professional to proactively perform and ensure these preventive maintenance steps are in place and working on a monthly basis. This will prevent computer slowdowns and issues!
John Daniell and the Swordfish Computer Solutions team help people prevent computer slowdowns and resolve computer issues. They do this by providing IT outsourcing computer services including computer networking, repair, training, website development, and graphic design in Cincinnati, Ohio. John can be reached at http://www.SwordfishCS.com.
Personal Firewalls - Secure Your Computer
There has not been a time in the history of the personal computer that firewalls and anti-virus programs have been more necessary and in-demand. Today, personal computer security is not only threatened by viruses and worms, but also by spyware those severely annoying programs that are illegally loaded onto your computer from the internet. Spyware programs can seriously undermine the operating structure of your computer, as well as make you vulnerable to identity theft and other criminal activities. Firewalls, long since a staple in the corporate world for defending large, expensive internal intranets or other networks, has now come into its own as a tool for personal computer owners as well. Your home computer is just as susceptible if not more so to online attacks, so why should it not be protected?
What is a firewall, anyway?
For those of you who may not be as versed in the pc security lingual as some, we offer here a fairly simple definition. A firewall is a collection of security programs that act to block unauthorized users from gaining access to a particular computer network (or single computer). Most firewalls also comprehensively monitor and report the data transfers between the network and the outside internet environment. Thus, they are quite effective in keeping your computer or network safe, allowing you to access the internet without taking a high security risk.
Sygate Personal Firewalls
There are few highly reputable firewall providers out there, and Sygate is certainly one of them. Here we go over some of the features of the Sygate line firewalls, so that you may choose the best one for your pc or server.
Sygate currently offers two main personal firewalls: the Sygate Personal Firewall (SPF) and the Sygate Personal Firewall Plus (SPFP). The major differences between the two are the advanced features you will only find on the SPFP. With the Plus version you will get VPN support, intrusion detection system (IDS), active reponse, and anti-mac, anti-ip spoofing. Both versions of the software come with the material that any pc user should really make sure they have: the main "application" firewall, intrusion alarm system, attacker tracing system, and security policy customization. These features are what are really necessary for a firewall to protect your home computer. The firewall needs to be able to block outsiders from gaining access to your computer, and they need to alert you when an attack has been attempted (or is in progress). Considering that the SPF is essentially free to download, and contains the elements you really need, this is the application we recommend for home pc users. For small business networks, the more advanced features offered by the Sygate Personal Firewall Plus is certainly worth the $40.00 pricetag. Both options are solid firewall applications and can be highly trusted to perform well on nearly any system.
Norton Personal Firewalls
Sygates closest competition in the area of personal firewall is Norton. Norton anti-virus programs are very well known, and have largely carried the brand over the last decade. Although less well known, Norton offers a powerful and comprehensive firewall program for home pc owners. Norton Personal Firewall 2005 is similar to the Sygate Personal Firewall program mentioned above. Some of the neat features of this application include the Norton Privacy Control (which keeps information from being sent without your knowledge in email, instant messages, MS Office attachments, and various forms on the web, such as those you enter your credit card number in), and intrusion prevention system that automatically blocks suspicious incoming traffic (from hackers, etc.). If this product is anywhere near as well designed and engineered as the anti-virus programs from Norton, then it is definately worth a look. The software can be downloaded or ordered online for $49.
Bradley James is a senior editor at SciNet.cc, a website containing many helpful consumer electronics review articles. For more information on personal firewalls, please visit our personal firewall webpage.
Registry Cleaner: Protection for Your PC
Your personal computer saves all the processes that are happening within it. The operating system has its own log of these programs running, and changes that are happening within it. What is a registry cleaner? First you must understand what a registry is. A registry is an applet within your compendium pack of an operating system. Within the term itself registry registers the processes that take place. It also takes note of the automatic processes that are happening in your PC and are running in the background. Think of the registry as a big notebook of your PC's to-do list and it logs everything into it.
Why a registry cleaner important? Registry cleaners are important because it protects your PC from other processes that are not considered viruses, but can be harmful to your PC. Is your computer slowing down without your knowledge? Are you having errors that are not distinguished by your anti-virus program? Your PC might be affected by applications that are running without your knowledge. Registry cleaners are a must!
Your PC might be inflicted by Adwares, Spywares and Spambots. In addition, your registry might be littered with logs that commands your PC to execute these files. A registry cleaner is needed to clean some of these programs. Registry cleaners detect errors in your PC. Registry cleaners help your PC function properly and registry cleaners detect errors, and deletes and or fixes them. For your PC to function in its optimum performance, you must have a registry cleaner. The basic programs that your PC should have in order to function properly should be: anti-virus software, firewall, anti-spam, and a good registry cleaner.
When your PC suddenly has a mind of its own, it might have caught a Spyware, or an Adware from the internet. Spywares and adwares are small programs that download themselves from the internet to your PC. They affect your PC's registry and a registry cleaner can possibly fix the errors that they cause. Spywares monitor your PC's activity? the programs running, registry information, websites visited. Adwares are annoying pop-ups and spam mails. Registry cleaners often block these from proliferating in your PC. These programs are not considered virus by your anti-virus, but it tinkers your PC's registry, and sometimes cause errors.
A registry cleaner fixes bugs or errors that are inherent in your PC. If you don,t have a registry cleaner, your PC will function at a slower rate. Also, without a registry cleaner, a PC will be inflicted with many annoying programs that run on the background. A registry cleaner scans, identifies and fixes the bugs that are contained in your operating system's registry. Some of the bugs in your PC are actually from other programs that you have installed. Sometimes, your PC is running programs that are non-existent anymore. Installation and uninstallation processes also affect your PC's performance. Registry cleaners also deal with these errors. Sometimes, files are corrupted when you uninstall. Some PC's even restart on their own, behaving erratically and uncontrollable. If you have these problems, you need a registry cleaner.
Registry cleaners are softwares. You can download free registry cleaners in the internet. But it is advisable to buy a licensed registry cleaner because it offers better technical support. Crashes are inevitable without registry cleaners. Losing all your data, or having a corrupted program is a nightmare, so be wise, have a registry cleaner!
Irene Graham is the owner of Free Internet Eraser. To learn more about using registry cleaners to protect your PC, go to: http://free-internet-eraser.com
Small Business Computer Security, the Basics
Anyone in business today realizes both the natural dependency on computers in the workplace, and also the potential dangers associated with storing important data on them. Todays business owners are constantly being reminded that their companys data is at risk by the daily reports on various news stations, or even their favorite business-related website.
But what can a typical small business owner do to protect their network from these threats that are broadcasted in so many ways? Dangers lurk at every turn on the Internet. There are thousands of attacks or areas of security that could be discussed, but I am going to try and focus on three general nuisances associated with todays computers: viruses, spy-ware, and traditional hackers that will intentionally try to exploit your computer systems for various reasons. All of these attacks, although different, serve a specific purpose for the attacker, yet basically translate into three things for a business: lost productivity, lost data, and the end result lost money.
Here is brief descriptions of what the aforementioned attacks are, consist of, and what a typical small business can do to protect their technology investments.
Virus: A computer virus shares some traits with an actual virus that gets people sick. A computer virus must piggyback on top of some other program or document in order to get executed. Once it is running, it is then able to infect other programs or documents. Obviously, the analogy between computer and biological viruses stretches things a bit, but there are enough similarities that the name sticks. A computer virus can have many intentions. One common goal is the viruss desire to infect as many machines as possible. Some are harmless and are no more then an attempt for a hacker to spread their name and get recognition amongst their peers. However, this can still lead to slow computer performance or programs acting up. On the other side of the coin, viruses can be extremely harmful and delete data, cause complete computer interruption, give someone unauthorized access to your company data, or even be used in conjunction with thousands of other infected computers to launch grand-scale attacks. Viruses are still mostly transferred via email; however newer attacks will entice you via an email to a malicious website that will exploit a flaw in your computer to install the virus.
Protection from Viruses: If you are reading this article, and you still do not have current (this is very important) anti-virus software running on EVERY single computer you own, then shame on you. With all of the marketing commotion that surrounds viruses, you should already have antivirus software on all of your computers. If you dont, then hurry to the store and purchase it. Popular software in the antivirus market is made by Symantec (www.symantec.com) and McAfee (www.mcafee.com). Larger companies may look into a system that will scan emails prior to the email getting to a users inbox for viruses. Also, be wary of what you open in your email. Do not open emails from people you do not know, and even if you do know the sender, take extra caution, as most viruses today will trick you into believing that the virus is sent from someone that you know.
Spyware: You may know spyware by one of its many names, adware, malware, trackware, scumware, thiefware, snoopware, and sneakware. Because of its stealthy nature, most Internet users are more familiar with the symptoms of spyware infection: sluggish PC performance, increased pop-up ads, unexplained homepage change, and mysterious search results. For virtually everyone surfing the Internet, malware and adware are a nuisance, but if you do not detect spyware on your PC, it can lead to much more serious consequences such as identity theft. Many people wonder how they get spyware installed onto their computer in the first place. Typically, spyware is installed onto your PC without your knowledge because the programs are usually hidden within other software. For example, when you are browsing a website, and a pop-up appears to install the latest online Casino game, it probably will give you that game, but youve also just installed spyware along with that. Another avenue for Spyware to infect your machine is through popular Peer-to-Peer File Sharing software such as Kazaa. The financial impact on a business that is plagued by spyware can toll very high. Costs paid to computer consultants to remove spyware, and a users overall lost of productivity from a slow-performing computer can add up very quickly.
Protection from Spyware: Spyware is a huge problem in todays computing environment. Fighting Spyware starts with smarter use of your computer. The best defense against spyware and other unwanted software is not to download it in the first place. Here are a few helpful tips that can protect you from downloading software you don't want. Only download programs from web sites you trust, read all security warnings, license agreements, and privacy statements associated with any software you download, and never click "agree" or "OK" to close a window. Instead, click the red "x" in the corner of the window or press the Alt + F4 buttons on your keyboard to close a window, and be wary of popular "free" music and movie file-sharing programs, and be sure you clearly understand all of the software packaged with those programs. If you do happen to install Spyware on your computer, there are some tools available to assist in the removal of spyware. Be careful however when downloading these free spyware removal softwares, as even some of the removal tools incorporate spyware into their software. A popular product that does a good job of removing spyware is Lavasofts Adaware (www.lavasoft.com). Larger organizations can look to companies such as Computer Associates (www.ca.com) for enterprise protection. There are instances when there is simply just too much spyware installed on a machine where these tools cannot help, and youll be forced to format your hard drive and reinstall your operating system.
Hackers: The term hacker has many different meanings to many different people. A dictionary might define the word hacker as follows, A person who breaks into, or attempts to break into, or use, a computer network or system without authorization, often at random, for personal amusement or gratification, and not necessarily with malicious intent. 2. [An] unauthorized user who attempts to or gains access to an information system 3. A technically sophisticated computer expert who intentionally gains unauthorized access to targeted protected resources, loosely, a computer enthusiast. 4. A person who uses a computer resource in a manner for which it is not intended or which is in conflict with the terms of an acceptable-use policy, but is not necessarily malicious in intent. As you can see, a hacker is someone with a very high aptitude in computing. By studying the inherent design of computer systems, a hacker will then attempt to compromise those systems for a purpose. Typically, they use a collection of tools easily downloadable on the Internet to exploit a flaw in a program or hardware system. Hackers do what they do for various reasons. Some do it for simple prestige amongst their peers, others for financial gain, and others do it to make a political statement. The impact of your networks security being breached can lead to very serious financial losses. Imagine your customer database being sold to a competitor or even what public response would be if you had to tell your customers that their personal information was stolen?
Protection from Hackers: I was once told, that no matter how good a safe you buy, there will still always be a locksmith that can un-lock it. The same goes for protection against hackers. However the amount of people with the expertise to bypass most security defenses, available to companies, are few and far in between. To keep your network safe, the following three items are an absolute must. A quality firewall at your networks perimeter to filter what goes in and out of your internet connection, desktop level firewalls to keep internal company computers safe, and the importance of performing updates to your computers operating system and applications. Firewalls simply stated, filter data passing through them. They are in essence, inspectors that allow and deny data to be passed through them based on certain rules. Most quality firewalls will protect your network by letting the good data through and keeping the bad out. Recommended firewalls for small businesses can be purchased from companies such as Cisco (www.cisco.com), Watchguard (www.watchguard.com) or Sonic Wall (www.sonicwall.com). Firewall vendors typically have many different models available, so consult with your network security professional on what to buy. The important thing is that you have one in place. Desktop level firewalls provide a true multi-layered approach to security. This added level of protection strengthens your computer systems defense, and is especially helpful to companies that have remote workers. Most companies today do have firewalls on their corporate network; however no one ever thinks about the company presidents laptop that gets brought home everyday. The president brings his laptop home and sets up his trusty remote connection back into his office over his broadband home Internet connection. The once protected laptop is now completely unprotected and connected directly to the corporate office, which gives a direct avenue for virus and hackers onto your corporate network. The great thing about desktop firewalls is that you can get some great ones for free! If you use the Microsoft Windows XP operating system, simply upgrade to service pack 2 and it includes a free and easy to use desktop level firewall. If you do not have Windows XP or just do not want to use their firewall, Zone Alarm (www.zonealarm.com) offers a great desktop level firewall. The last level of defense is to keep your networked systems up to date with the latest patches and fixes from their respective manufacturers. I will assume that most companies use Microsoft Windows products for most of their computing needs, so to keep your system updated simply go to http://windowsupdate.microsoft.com. You should check for updates twice a month.
Even though this article simply brushes the surface of network security, I hope it gives you insight as to some potential dangers out there and real incentive to implement better security for your company. Just as you have an alarm system at your office, please take the necessary steps to protect your companys computer network and data. If not, the costs of recovery I guarantee you will far exceed the costs to implement a secure network.
Jarrett M. Pavao studied at the University of Miami, is a Microsoft Certified System Engineer, and Citrix Certified Administrator. Jarrett is the Director of Business Technologies for Docutek, a systems integrator in Boca Raton, FL. Jarrett can be contacted at jpavao@docuteksolutions.com with any network security related questions or concerns.
Jarrett M. Pavao studied at the University of Miami, is a Microsoft Certified System Engineer, and Citrix Certified Administrator. Jarrett is the Director of Business Technologies for Docutek, a systems integrator in Boca Raton, FL. Jarrett can be contacted at jpavao@docuteksolutions.com with any network security related questions or concerns.
Is Your Computer Sick?
Viruses and spyware usually show up on your computer one of two ways.
Either they invade your system with a frontal assault like the Huns attacking the Romans, or they sneak in a back door like a cat burglar.
Either way, once a virus or piece of spyware gets on your system, getting it off can rate harder than curing a severe case of trench foot!
Viruses, malicious programs designed to disrupt normal computing, and spyware, programs intended to literally "spy" on your activities, can enter your computer a number of ways.
Most commonly they enter your system through an email attachment, by sharing files with an infected computer by disk, as a "ride along" with a 3rd party program you install, or through a "back door" port in your computer.
Regardless of how they get on your system, once in place, they cause no end of headaches and frustration.
The following represent typical signs you may suffer from infection by a virus or piece of spyware.
Your computer starts acting oddly by doing things it never did previously.
Your modem starts trying to dial out to the Internet without you initiating a surfing session.
You notice that files start disappearing, the system stalls, runs slowly, or even crashes frequently.
Your computer takes progressively longer to boot up every time you start it or you notice that your available hard drive space has disappeared. Strange popup windows appear, even when you're not surfing the web, or you delete a program and it "magically" reappears next time you boot the system.
If you suspect you a virus or a piece of spyware has invaded your computer, follow these steps to first identify and then delete the offending code:
Step 1 - Back up your important files, but remember to scan these files for viruses before reinstalling to avoid accidentally re-infecting your system.
Step 2 - Update your anti-virus definitions and perform a scan of your hard drive.
If you don't carry virus protection, or you suspect your anti-virus software got corrupted somehow, then log on to www.pandasoftware.com and use the free Panda Active Scan service to check your hard drive for viruses.
Follow the instructions for quarantining and removing the offending files.
Step 3 - Scan your hard drive with an adware, scumware, or spyware detection and removal tool like Adaware www.lavasoft.de/support/download/ or Spybot http://spybot.safer-networking.de/.
Step 4 - In many cases, when the virus or spyware program gets installed with a free utility or game you download from the Web, you must usually uninstall the utility or game to finally get rid of the problem once and for all.
Step 5 - Avoid re-infection by keeping your anti-virus and firewall up-to-date at all times.
As a last resort, if you run into a program you simply can't get rid of, but can figure out the offending file's name, do a search for the file name on Google.com. Often you will find you're not the first victim and may get valuable advice for cleaning up your system.
However, be very careful of the information you find and think twice before modifying any system files.
About The Author
Jim Edwards is a syndicated newspaper columnist and the co-author of an amazing new ebook that will teach you how to use fr^e articles to quickly drive thousands of targeted visitors to your website or affiliate links...
Need MORE TRAFFIC to your website or affiliate links? "Turn Words Into Traffic" reveals the secrets for driving Thousands of NEW visitors to your website or affiliate links... without spending a dime on advertising! Click Here> http://www.turnwordsintotraffic.com
Basic Steps To Optimize Your Internet Security
After seeing many people complain about their weak Internet security I decided to write down some things that will help you for your Internet security.
First, here are some tips to make windows safer :
For basic security and update patches install Service Pack 2 for Windows XP or Service Pack 4 for Windows 2000.
Once a month use Windows Update so you can get the latest pacthes.
When you download software from the Internet make sure you download it from the original website.
Always run anti Trojan and anti virus software.
Even if you don't use it you have to make your Internet Explorer as safe as possible.
When you access the Internet you are browsing the web using a browser such as Internet Explorer. The Internet Explorer contains several security vulnerabilities. You should make it as safe as possible or switch your default browser to an alternative. You will have to set some options from the Manage Add-Ons in the Internet Options. You will see a list of add-ons that can be activated or deactivated. If you see any unusual entries just deactivate them so you can be sure you don't have a trojan/worm.
Under Internet Options -> Security -> Internet -> you will see the Edit Level.You should set it to high in order to disable most of the security threats.
Your Web Browser should be ok now. Let's see what we have to do from our email point of view.
Because it's built-in in their Windows system lots of users like to use Outlook Express for emailing. But it's a fact that it contains many security vulnerabilities so I advise you to use alternatives. If you use a web based Email (you can browse your email with your web browser) you can delete viruses even if you don't download them to your PC.
Make sure you have installed an Anti Virus for 100% virus protection. One that I've found to be very good and never disappointed me is the AVG Anti virus. If you take the time to regularly update it you will be safe enough with it.
Lots of people install Firewalls because they belive their Internet security will be higher. I personaly disagree. If you do not know how to best configure it, and you have to know much about the tech behind it to do so, it will just make your PC slow and software not working.You can just use the Windows XP SP2 firewall for basic security.
All this tips should make your PC safer. I browse the Internet every single day for some time now and they worked great for me. I haven't met a virus/worm for some time now.
DSW Distribution Ltd has all you need for your internet security: mcafee antivirus, norton antivirus 2005, microsft office 2003 standard edition, panda antivirus, windows xp and many more ...Visit us at http://www.dswtrade.com
Finding the Perfect Anti-spyware Software
Fortunately, there are generous individuals and organizations who have the facilities to review the work of the Anti-spyware developers and make the results available for all of us everyday users of the Internet.
The challenge for us is to know where to go for these results and recommendations, and to know which of the anti-spyware and anti-virus programs to use on our computers.
There are many web masters, newsletter, and Blog publishers who constantly monitor the results published by the anti-spyware reviewers. Most of them pass these information alerts on to their readers and subscribers, often offering suggestions and advice based on their own personal experiences and expertise.
A real benefit for us is that most of the top rated anti-spyware and anti-virus programs are free, or available in Trial or Demo versions.
All we need do is find out where to get them. But first, we need to find the reviewers who post the alerts.
If subscribing to newsletters and Blogs isn't your usual surfing activity, you can do a search for security alert newsletters or security alert blogs. For example, do a Yahoo search for "security alert newsletter" (use the quotation marks to get the most appropriate search results). Do the same for a Yahoo or Google search on "security alert blog". (Blogs are web logs).
Investigate the first and second pages of the search results and select three or four of the listings as a starting point. Many newsletters are published on a monthly schedule and may not contain the most current information. Some are published weekly. They may be better choices.
Blogs are usually much more current since Blog authors often post their information every couple of days - some even on a daily basis.
Blogs are riding a major wave of popularity. For the serious searchers of current information, this is a great benefit. There aren't as many Blog sites as web sites yet, so it's often much easier to find the information you're looking for.
Many Blog authors make their publications available for RSS (Real Simple Syndication) readers. If you have added a RSS reader to your browser, you can get up-to-the-minute alerts presented to you automatically. You don't need to go looking for them.
Many updated browsers, like Netscape 8 and Firefox include this feature as part of their package. Expect the newest Internet Explorer to have a RSS Reader, too.
Don't be overwhelmed by all of the information you get. After doing these searches and reviews once or twice, it will be a simple task to select what you need to keep yourself current.
For starters, it is generally accepted practice to select and use at least two anti-spyware programs. Choose from among the two or three that receive the highest recommendations and ratings from the newsletter and Blog authors. Be especially watchful for and select one of those programs that provides 'Real Time' monitoring. (Which means that they monitor and catch any incoming bugs that may try to infect your machine while you are online).
Downloading instructions are nearly always present with the reviews. If not, you'll find sites like c|net.com to be a good source for download links.
Just don't forget to check for and update your security software. The spyware writers won't give you a break if you do.
Supportcave.com offers new and enhanced Spyware Removal Software. Not only will these programs effectively check and clean your computer from Spyware, once installed they will also shield your computer from future Spyware intrusions and browser hijacks - before the malevolent software even have a chance to enter you PC! Spyware Remover Software is an important function all computer users should rely on to ensure their computer is free from nosey software and their privacy protected.
Internet Privacy
Over the past few years as the internet has become more and more popular, privacy has become a major issue. Just as if you are walking down the street and can be watched, every click of your mouse every website you browse, or file you download, is traceable. In recent years this has become a major issue.
Spyware:
The most currently talked about privacy issue at the moment. Spyware are little programmes that can easily be picked up by surfing any website or downloading files. Spyware can pickup information from where you surf to your credit card details, this information then can be sold.
Generally only the "Dodgy" websites give you Spyware but people are now creating harmless looking websites with real content but only offering a download that may be Spyware. There are many developers trying to create software that will infiltrate the Spyware and take it out, but just as smart these coders are so are the Bad guys. Microsoft are waging war on Spyware by developing their own free downloadable Spyware remover, but already in the beta stages, viruses have been made to stop Microsoft's Anti-Spyware programme in its tracks. This is the lengths these malicious coders will go to, to keep their piece of the pie.
Cookies:
Cookies sounds like something yummy, but on the internet cookies can be the opposite. Cookies are great tools as they allow websites to recognise you when you come back to view their pages.
The major issue with this is some webmasters collect data on you from passwords to private and personal information. Cookies can even help nasty people to steal your identity.
In 2003 Identity Fraud World Wide was estimated to be approximately $100 Billion USD. By the end of 2005 it is estimated identity fraud will cause up to 5 Trillion Dollars World Wide..
It is totally important to protect yourself online. There are plenty of decent quality Spyware removal tools. My current favourite is Ad-Aware, which does a very good job of removing Spyware, and the programme even keeps it self up to date with the latest definitions.
A few more things to keep in mind:
Keep your Anti-Spyware and Anti-Virus software up to date.
Regularly run your Anti-Spyware and Anti-virus programmes.
Only submit Private and Personal information to Secure Websites.
Never give out any personal information to non trusted websites.
Clear your internet browser cache regularly.
Never assume anyone is as honest as you.
Steve
Private Mail services
http://www.private-services.com
Personal Firewalls for Home Users
What is a Firewall?
The term "firewall" illustrates a system that protects a network and the machines on them from various types of attack. Firewalls are geared towards keeping the server up all the time and protecting the entire network.
The primary goal of a firewall is to implement a desired security policy; controlling access in both directions through the firewall, and to protect the firewall itself from compromise. It wards off intrusion attempts, Trojans and other malicious attacks.
Personal Firewalls:
They are meant for the home user in a networked environment. They aim to block simple attacks, unlike the enterprise level firewalls that the corporate world uses at the server or router end. There are many ways to implement a firewall, each with specific advantages and disadvantages.
Are they really needed?
Nowadays organizations and professionals use Internet technology to establish their online presence and showcase their products and services globally. Their endeavor is to leverage digital technology to make their business work for them.
All the organizations and professionals are shifting from Dialup to broadband and getting a fixed IP. It has led to an increase in security attacks, bugs in everyday working. This does not mean that Dialup being anonymous dynamic link or the firewall of the ISP network make you pretty safe.
Now if your machine was under attack, you must have wondered what went wrong making your system crash suddenly. So I would rather like to say, its not necessary for anyone to actually know about you or your IP address to gain access to your system.
If you system is infected or prone to intrusions, then beyond the anonymity of your Dialup connection or a dynamic IP, your system can be hacked.
Types of Attacks
Intrusion:
There are many ways to gain unauthorized access to a system. Operating system vulnerabilities, cracked or guessed passwords are some of the more common. Once access is attained, the intruder can send email, tamper with data, or use the system privileges to attack another system.
Information Theft and Tampering:
Data theft and tampering do not always require that the system be compromised. There have been many bugs with FTP servers that allow attackers to download password files or upload Trojan horses.
Service Attacks:
Any attack that keeps the intended user from being able to use the services provided by their servers is considered a denial of service attack. There are many types of denial of service attacks, and unfortunately are very difficult to defend against. "Mail bombs" are one example in which an attacker repeatedly sends large mail files in the attempt at filling the servers disk filesystem thus preventing legitimate mail from being received.
Types of Attackers
Joyrider:
Not all attacks on computer systems are malicious. Joyriders are just looking for fun. Your system may be broken into just because it was easy, or to use the machine as a platform to attack others. It may be difficult to detect intrusion on a system that is used for this purpose. If the log files are modified, and if everything appears to be working, you may never know.
Vandals:
A vandal is malicious. They break in to delete files or crash computer systems either because they don't like you, or because they enjoy destroying things. If a vandal breaks into your computer, you will know about it right away. Vandals may also steal secrets and target your privacy.
In an incident a Trojan was being used to operate the web cam. All the activities being done in the house were being telecasted on the websites.
Spies:
Spies are out to get secret information. It may be difficult to detect break-ins by spies since they will probably leave no trace if they get what they are looking for.
A personal firewall, therefore, is one of the methods you can use to deny such intrusions.
How Firewalls work?
Firewalls basically work as a filter between your application and network connection. They act as gatekeepers and as per your settings, show a port as open or closed for communication. You can grant rights for different applications to gain access to the internet and also in a reverse manner by blocking outside applications trying to use ports and protocols and preventing attacks. Hence you can block ports that you dont use or even block common ports used by Trojans.
Using Firewalls you can also block protocols, so restricting access to NetBIOS will prevent computers on the network from accessing your data. Firewalls often use a combination of ports, protocols, and application level security to give you the desired security.
Firewalls are configured to discard packets with particular attributes such as:
- Specific source or destination IP addresses.
- Specific protocol types
- TCP flags set/clear in the packet header.
Choosing a firewall:
Choose the firewalls which have the ability to ward of all intrusion attempts, control applications that can access the internet, preventing the malicious scripts or controls from stealing information or uploading files and prevent Trojans and other backdoor agents from running as servers.
The purpose of having a firewall cannot be diminished in order to gain speed. However, secure, high-performance firewalls are required to remove the bottleneck when using high speed Internet connections. The World-Wide-Web makes possible the generation of enormous amounts of traffic at the click of a mouse.
Some of the good firewall performers available in the market are below:
- BlackICE Defender
- eSafe Desktop
- McAfee Personal Firewall
- Neowatch
- Norton Personal Firewall
- PGP Desktop Security
- Sygate Personal Firewalls
- Tiny Personal Firewall
- Zone Alarm
- Zone Alarm Pro
Most of these firewalls are free for personal use or offer a free trial period. All the personal firewalls available cant ensure 100% security for your machine. Regular maintenance of the machine is needed for ensuring safety.
Some of the tasks advised for maintaining system not prone to intrusions:
- Disable file and print sharing if you are not going to be on network.
- Update your antivirus signature files regularly.
- Use a specialized Trojan cleaner.
- Regular apply security patches to your software and operating system.
- Dont open email attachments if you have dont know the contents it may contain.
- Dont allow unknown applications to access to the internet or to your system.
- Regularly check log files of your personal firewall and antivirus software.
- Disable ActiveX and java and uninstall windows scripting host if not required.
- Turn off Macros in Applications like Microsoft Office and turn macro protection on.
- Check the open ports of your system and see them against the common list of Trojans ports to see if they are being used by some Trojan.
- Log Off from your internet connection if not required. Being online on the internet for long duration gives any intruder more and sufficient time to breach system security.
- Unplug peripherals like web cam, microphone if they are not being used.
About The Author
Pawan Bangar,
Technical Director,
Birbals,India
ebirbals@gmail.com
Be Prepared in the Event Computer Disaster Strikes
Computers
Businesses and individuals alike have all grown to rely on computers. The reliance is never more apparent than when something happens to the horrid little box that makes our lives easier. We expect computers to react a certain way, in certain situations. It nearly always comes as a surprise when the beloved little box, know as a computer, refuses to boot up. Probably even more shocking, is the dawning that we've neglected to backup or prepare for the unforeseen disaster that has just been thrust upon us.
Regardless of the number of times you have experienced the dread of being unable to access the information trapped in the god-awful computerized contraption, we are always invariably unprepared.
The reality of it is that computers, not only contain moving parts, but they like other machines, they are prone to failure at some point in their lives. Not only can hardware failures occur, but viruses can also corrupt data making it impossible to retrieve. Regardless of the litany of words used to bully the box into behaving, the truth is that the only offence is a good defense.
So how do you prepare for a computer tragedy?
Prepare for the Worst
In structuring an offense it's important to realize the power of reinforcements: backups are invaluable and will save countless hours of shameless degradation. Be sure that you backup data and files on a regular basis, there are a number of tools that will automate the process.
It is critical that you check the backup log to ensure that a backup was completed properly. I cannot begin to describe the devastation felt when it is realized that though there was a backup process in place, the backup never actually occurred. Realizing this during a restore is likely to push any computer lover over the edge. It is a good idea to store a weekly back up off site. This is especially helpful, if an unforeseen fire or a natural disaster strikes.
Protection is critical!
Build A Wall
If the computer has Internet access, either a hardware or software firewall (or combination there of) must be used. The firewall creates a barrier between a computer and the world. Without a firewall, Internet worms are capable of exploiting security holes and are able to create what are referred to as 'back doors'. These back doors can then be used to gain access to personal information stored on the computer, including password files, and financial information.
Trust No One
If you are an avid Internet surfer or downloader be sure to scan any downloads prior to opening or installing. Up to date anti-virus software should be used to ensure, that computers do not become infected with malicious viruses that will ruin your life. Scan any email attachments prior to opening regardless of whom they are from. Files that end with .scr, .pif and .exe can contain viruses that will wreak havoc with your data and emotional well being.
Preparedness goes a long way, and a little foresight will ensure that, while a computer might be an inconvenience, you will not be defeated.
Preparation Resources
Anti-virus Software -http://www.military-software.com/anti-virus-software.htm
Firewalls - http://www.monitoring-software.net/intrusion-detection-software.htm
About The Author
Sharon Housley manages marketing for NotePage, Inc. http://www.notepage.net a company specializing in alphanumeric paging, SMS and wireless messaging software solutions. Other sites and additional articles can be found at http://www.softwaremarketingresource.com , and http://www.small-business-software.net
Secure Your PC From Hackers, Viruses, and Trojans
Viruses, Trojans and Spyware: Protecting yourself.
No user on the internet is safe from assault. Viruses, Trojans and Spyware can all effect your computer by placing annoying ads, tracking your credit card numbers, or even slow it down to a certain extent it is deemed no longer usable. By following through these simple steps, you can help protect yourself from the internet.
High CPU Usage: If your computer seems to be slower than usual, it is very likely that you have been infected. Background services can slow down your computer, and to check performance, enter Task Manager (Ctrl+Alt+Delete). Then, click on the processes tab. You will be able to see active processes that are running. To find what should be running on your computer, visit http://www.theeldergeek.com/services_guide.htm.
Check your level of protection: A good way to know whether you are safe or not is by using security tools. Here are some you should try out: NeWT 2.1: This is a very simple tool to use, and it scans for more than 4000 common security vulnerabilities. Download NeWT here: http://www.tenablesecurity.com/newt.htm Sumantec security check: This is a free service provided by Symantec. Simply visit here (www.sumantec.com), then select Scan for Security Risks. It will only tell you what vulnerabilities you have, but however it won't tell you how to fix them. Infinitive! Port Scanner: Our very own online port scanner! http://infinate.x10hosting.com/phport
Update Yourself: Install all the latest update possible. Service Pack 2 is a good way to start if you're running Windows XP. Enable Automatic Updates, and make sure you have the latest updates on your PC.
Safe Surfing: Due to Internet Explorer's high popularity, it is usually safe to change altogether. A common program now is known as FireFox (www.mozilla.com/products/firefox), which is fast, responsive and similar to Internet Explorer. However a major flaw with FireFox is that you will need to install additional plug-ins in order for you to view certain pages.
Make Regular Backups: Prepare for the worst. Make regular backups of your important files and store them on a type of offline storage.
Don't open suspicious links: If you are sent a link you are not sure about, do not open them, Simple. Another good way is to avoid suspicious sites altogether. Many programs too, bundle with spyware, so when you download them make sure they are stated "Freeware", nothing else.
Program Protection: Use Anti-Virus and Firewall software. McAfee is a highly recommended product over Symantec, but there are also other free anti-virus/firewall software online such as NOD32. http://www.nod32.com/
If you have been infected: Find cleaning instructions online on sites such as http://vil.nai.com. It will tell you where to locate your infection, and where to find and remove it. System Restore is also a good option on Windows XP. To use System Restore, go to Start, All Programs, Accessories, System, System Restore. Simply click a restore point and reboot.
You can also remove viruses using the programs listed under Program Protection. To remove Spyware, Spybot S&D (http://www.safer-networking.org/en/index.html) is a free yet useful tool to use.
All articles are written by Infinitive!
Infinitive! http://www.infinate.x10hosting.com You may reproduce and use this article just so long as you add a link (http://www.infinate.x10hosting.com) down at the bottom.
Infinitive! All the latest articles, tools, news, file hosting and more!
All the Spyware Security You Need: For Free
More and more internet users are understanding how important it is for them to find security software that allows them to remain invisible to possible intruders. Threats such as spyware, Trojans, viruses, worms and other malware are difficult to avoid because they have become so widespread. To partially prevent these malicious codes from sneaking in you must first secure you computer with a firewall that will notify you of any unauthorized intruders.
Even by setting up your security so that you remain invisible to most intruders, users will be exposed to spyware and viruses by visiting web sites and downloading freeware and shareware. If you computer is invaded by spyware or viruses you must download both anti-virus and anti-spyware software. Technology experts recommend using more than one spyware tool because its threats are so prevalent no one scanning tool can catch all infections. Utilizing two or more anti-spyware tools will help better protect your computer from the consequences of spyware build up.
Each of the security tools necessary to keep your internet surfing safe can be downloaded for free. Numerous anti-virus, anti-spyware and firewall programs can be downloaded for free and most offer equivalent protection to those you purchase.
Because all the tools necessary for security are free, there is no reason users should not take advantage of the safety nets.
Once you have your security tools in place you can run a test through a trustworthy source to ensure that your computer is virtually invisible online and secure from intruders.
Mitch Johnson is a successful freelance author that writes regularly for http://www.1st-in-remove-spyware.com/, a site that focuses primarily on spyware detection software, as well as tips on how to avoid spyware from popping up on your computer. His articles have also been featured on related spyware sites such as, http://www.best-in-spyware-detection.com/ as well as http://www.best-sypware-removal-reviews.com/
